How to Set Up DKIM for Email Authentication
Want to ensure your emails land in inboxes, not spam? Setting up DKIM (DomainKeys Identified Mail) is a must. DKIM authenticates your emails by verifying they’re sent from your domain and haven’t been altered during transit. Here’s what you need to know:
- What is DKIM? It’s an email authentication protocol using cryptographic signatures to verify email integrity and sender legitimacy.
- Why it matters: Over 80% of email providers like Gmail and Outlook require DKIM for better deliverability. It can boost inbox placement by 10–20%.
- What you need: Access to your domain’s DNS settings, a DKIM key pair (private and public keys), and admin access to your email server.
- Steps to set up DKIM:
- Generate a DKIM key pair (2048-bit recommended for security).
- Add the public key as a TXT record in your DNS settings.
- Configure your email server to sign outgoing emails with the private key.
- Test your setup to ensure authentication works.
Pro tip: Tools like Mailforge automate DKIM setup, saving time and reducing errors, especially if you manage multiple domains. Properly configuring DKIM not only protects your emails but also improves your sender reputation and email campaign success.
What You Need Before Setting Up DKIM
Setting up DKIM requires some preparation to ensure the process goes smoothly. From having the right access credentials to understanding the technical details, here's what you need to know before diving in.
DNS Management Access
To configure DKIM, you'll need administrative access to your domain's DNS management interface. This is where you'll add or modify TXT records to publish the DKIM public key, a crucial step for email authentication. Typically, this access is provided by your domain registrar (like GoDaddy, Namecheap, or Cloudflare) or your DNS hosting provider.
Most DNS providers offer user-friendly web interfaces for managing domain records. If you're part of an organization, your IT department might handle this for you. Keep in mind that DNS changes can take up to 48 hours to propagate. Some DNS providers may require TXT record values to be enclosed in double quotes or might automatically append the domain name, so double-check the record format before saving.
If you're managing multiple domains, tools like Mailforge can streamline the process. Mailforge automates DNS setup for DKIM, DMARC, SPF, and custom domain tracking, saving you the hassle of manually updating each domain's DNS settings.
Creating DKIM Keys
For optimal security, it's recommended to use a 2048-bit DKIM key. This key length makes it significantly harder for attackers to compromise your DKIM signature through brute-force methods. Shorter keys, such as 1024 bits, are increasingly discouraged.
A DKIM key pair includes:
- Private key: Used by your email server to sign outgoing messages.
- Public key: Published in DNS so recipient servers can verify the signatures.
You can generate DKIM keys using several methods:
- Tools provided by your email service provider
- Command-line utilities like OpenSSL
- Online DKIM key generators
- Admin consoles from platforms like Google Workspace or Mailjet
Once generated, ensure your private key is stored securely. Restrict access to trusted administrators, apply strong file permissions, and consider encrypting the key. Regularly monitor access logs and rotate keys if you suspect any compromise.
If you're using Mailforge, the service automatically generates and manages DKIM key pairs for you, eliminating the need for manual key generation or additional tools.
Email Server Setup Requirements
After handling DNS and key generation, make sure your email server is ready to implement DKIM. You'll need administrative access to your email server or sending platform to upload the private key and enable DKIM signing. For cloud-based platforms like Google Workspace or Microsoft 365, admin privileges are necessary to access authentication settings.
Here’s what’s typically required based on your setup:
- Dedicated email servers: Administrator or root access to modify configuration files and restart services.
- Cloud email services: Admin access to the provider's control panel or API.
- Third-party platforms: Permissions to integrate and enable DKIM signing features.
Many email service providers include built-in DKIM configuration tools to simplify the process. However, having the right permissions remains key.
Services like Mailforge handle DKIM, DMARC, and SPF setup automatically, ensuring configurations align with industry standards. This minimizes manual work and reduces the risk of errors that could affect email deliverability.
Before starting, check if your domain already has DKIM records in place. Some domains, especially those using major email providers, may already have DKIM configured. Review your current DNS records and email server settings to avoid duplication and ensure everything is correctly set up.
How to Set Up DKIM Records
Now that you've got the necessary access and understand the requirements, it's time to set up DKIM authentication. Follow these four steps to activate DKIM on your domain.
Step 1: Generate Your DKIM Key Pair
Start by creating your DKIM key pair for your domain. The private key will sign outgoing emails, while the public key will be added to your DNS to let recipient servers verify those signatures. For strong security, always use a 2048-bit key.
Here are a few ways to generate your DKIM keys:
- Email provider tools: Platforms like Google Workspace and Microsoft 365 offer built-in tools in their admin consoles to generate DKIM keys. These tools simplify the process and ensure compatibility with their systems.
- Online DKIM generators: These web-based tools can create key pairs for any email server. Just make sure you're using a trusted generator.
- Command-line utilities: For those comfortable with technical tools, options like OpenSSL give you full control over key generation.
If you're using Mailforge, this step is automated, saving you time and effort.
Once your keys are ready, securely store the private key. Limit access to authorized users, apply strong file permissions, and consider encrypting it. Remember, the private key must remain confidential, while the public key will be published in your DNS.
Step 2: Add the DKIM Record to DNS
Publish the public key in your DNS as a TXT record. It should be formatted as selector._domainkey.yourdomain.com with the value v=DKIM1; k=rsa; p=....
For example:
- Record Name:
mail._domainkey.example.com - Record Type: TXT
- Record Value:
v=DKIM1; k=rsa; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQC3QEKyU1fSma0axspqYK49unoN...
Follow your DNS provider's formatting rules. Some providers require the value to be enclosed in double quotes, while others handle formatting automatically. Log in to your DNS management console, create the TXT record, and double-check the selector to avoid errors.
Keep in mind that DNS changes can take up to 48 hours to propagate. If the record doesn't show up immediately in DNS lookup tools, give it some time before retesting.
For those managing multiple domains, platforms like Mailforge simplify this step by allowing bulk DNS updates, making it easy to configure DKIM records across multiple domains.
Once your DNS record is live and propagation is complete, you can move on to setting up DKIM signing on your email server.
Step 3: Configure DKIM Signing on Your Email Server
Now, configure your email server or sending platform to sign outgoing emails with your private key. This process varies depending on your setup:
- Dedicated email servers: If you have admin or root access, upload the private key and adjust the configuration files. Popular servers like Postfix, Exim, or Microsoft Exchange include built-in DKIM support that can be enabled through configuration changes.
- Cloud-based email services: Platforms like Google Workspace and Microsoft 365 offer user-friendly admin interfaces. For example, in Google Workspace, you can navigate to DKIM settings, confirm your DNS record, and enable signing.
- Third-party platforms: Many email services allow you to upload your private key, specify the selector, and enable DKIM signing directly from their account settings.
When configuring DKIM signing, ensure:
- The selector in your server settings matches the one in your DNS record.
- The private key corresponds to the public key published in DNS.
- DKIM signing is enabled for all outgoing emails from your domain.
After making changes, restart your email service if necessary. If you're using Mailforge, this process is automated when you add a domain.
Step 4: Test Your DKIM Setup
Testing your DKIM setup is crucial to confirm that recipient servers can verify your email signatures. Here's how to test:
- Send a test email: Use your domain to send an email to an external address, like a Gmail account.
- Check the email headers: In Gmail, open the email, click the three-dot menu, and select "Show original" to view the headers. Look for the
DKIM-Signaturefield to confirm the email is signed. - Review authentication results: The
Authentication-Resultsheader should show "dkim=pass" or a similar success message. - Use external tools: Websites like mail-tester.com provide a detailed analysis of your email authentication, including DKIM validation.
If you run into issues, common problems include DNS propagation delays, selector mismatches, or incorrect private key setup. Wait for DNS propagation to complete before troubleshooting.
Regularly monitor your DKIM results to catch any issues early. With Mailforge, testing is straightforward, and positive results are typically immediate after setup, ensuring everything is correctly aligned.
Fixing Common DKIM Problems
Even with a meticulous setup, DKIM authentication can sometimes fail. These failures often stem from a handful of common issues. By understanding these pitfalls and their solutions, you can address authentication failures efficiently and maintain smooth email delivery. Below, we’ll explore three frequent trouble spots: DNS record formatting, propagation delays, and server configuration errors.
DNS Record Format Mistakes
Errors in DNS record formatting are one of the most common reasons for DKIM failures. Even small missteps in your TXT record can stop recipient servers from verifying your email signatures.
Some typical formatting mistakes include incorrect selector names, leaving out the "._domainkey" suffix, and using improper quotation marks. For instance, some DNS providers require the entire TXT value to be wrapped in double quotes, while others handle formatting automatically. Additionally, any line breaks or extra spaces in the public key can disrupt proper authentication.
Here’s an example of what a correctly formatted DKIM DNS TXT record should look like:
mail._domainkey.yourdomain.com. IN TXT "v=DKIM1; k=rsa; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQC3QEKyU1fSma0axspqYK49unoN..."
When reviewing your record, make sure the following elements are in place:
- The selector aligns with your server configuration.
- The "._domainkey" suffix is included.
- The value begins with "v=DKIM1;".
- The public key is complete and free of line breaks.
Keep in mind that some DNS providers automatically append the domain name to the host field. This can result in duplicate domain entries if you’re not careful. To fix any formatting issues, adjust your DNS record based on your provider’s specific requirements. Use online DKIM record checkers to validate the syntax before saving changes. Once you’ve confirmed the format is correct, consider whether propagation delays might be affecting the visibility of your record.
DNS Propagation Delays
After making DNS changes, it can take up to 48 hours for them to propagate globally, though most updates are visible within a few hours. During this time, DKIM authentication might fail intermittently as DNS servers update at different speeds.
To determine whether you’re dealing with propagation delays or configuration errors, use DNS lookup tools to check your DKIM record. If the record is inconsistent or missing, propagation delays are likely the culprit.
You can monitor the propagation process using tools like MXToolbox or by sending test emails to external accounts, such as Gmail. Look at the email headers to check the DKIM status. If you notice some emails passing DKIM checks while others fail, it’s a sign that propagation is still underway. Patience is key here - making additional changes during this period can lead to unnecessary complications.
If the record hasn’t appeared after 24 hours, wait another day before assuming there’s a deeper issue. If it’s still not visible after 48 hours, revisit your DNS formatting and provider settings. Once propagation delays are ruled out, turn your attention to server-side configurations.
Email Server Configuration Issues
Even with a flawless DNS setup, server-side problems can prevent DKIM from working correctly. Common issues include incorrect placement of the private key, failure to enable DKIM signing, and server misconfigurations that block outgoing email signatures.
To address these issues, ensure the private key is stored in the correct location with proper file permissions. Double-check that DKIM signing is enabled, either in your server’s control panel or configuration files. Also, confirm that the selector and private key match the published DNS record.
After making any changes, don’t forget to restart your email service to apply the new settings.
For organizations managing multiple domains, manual configuration can quickly become overwhelming. Tools like Mailforge simplify the process by automating DNS setup and bulk updates, reducing the risk of errors and making DKIM management more efficient across large-scale environments.
As you troubleshoot server-side issues, send test emails and inspect the headers for DKIM-Signature fields. If the signatures are missing, the problem lies with your server configuration, not your DNS records.
Managing DKIM at Scale with Mailforge
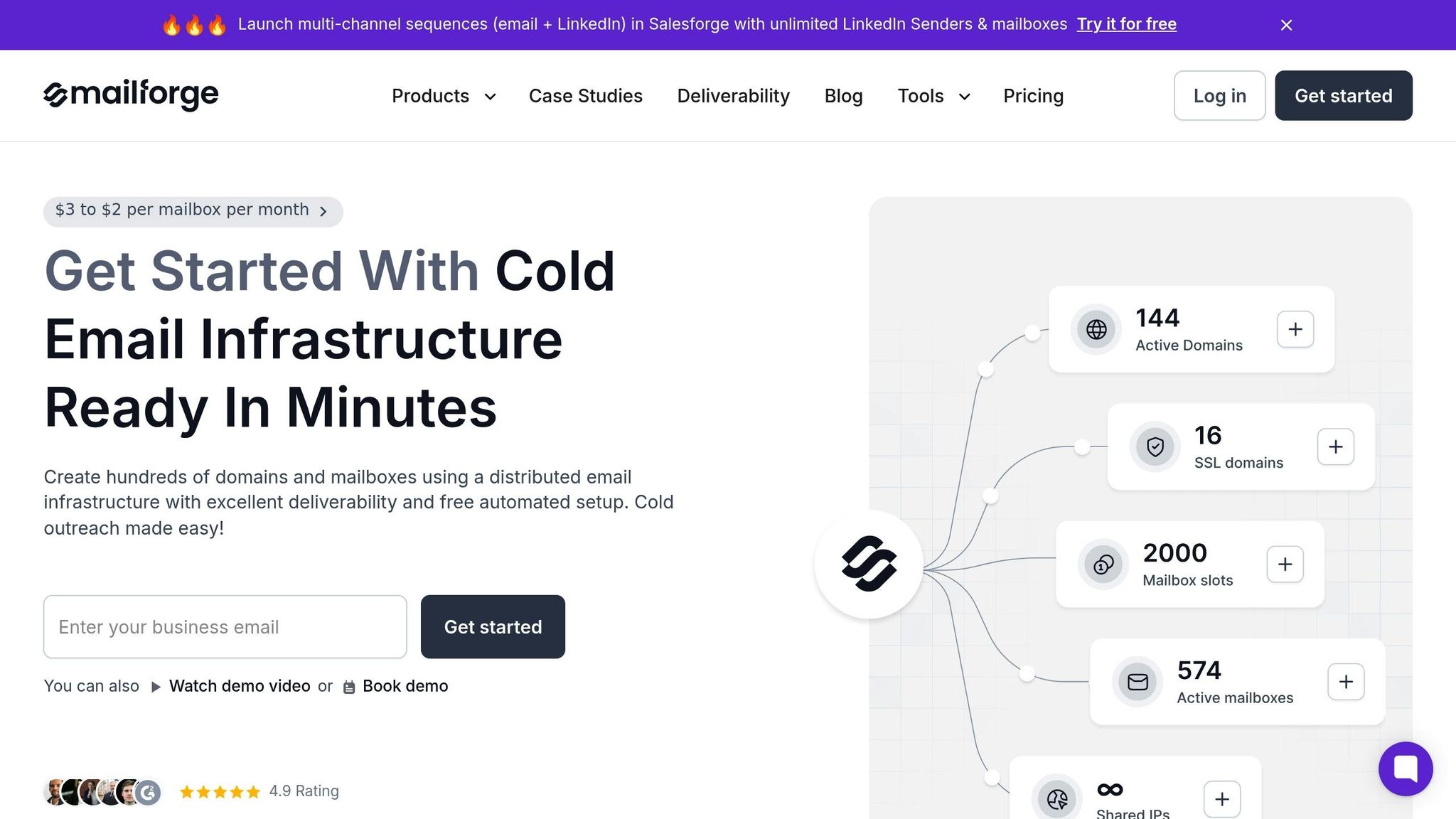
When you're managing dozens, hundreds, or even thousands of domains, setting up DKIM manually can quickly become overwhelming. Each domain demands its own key pair generation, DNS record setup, and server configuration. What might take a few minutes for one domain can stretch into days or even weeks when scaled up. Mailforge simplifies this process with automation, making DKIM management far more efficient for large-scale operations.
Automated DNS Configuration
Mailforge takes care of generating key pairs and creating DNS records for DKIM, SPF, DMARC, and custom domain tracking. By automating these steps, it eliminates common errors like mistyped selectors, missing the "._domainkey" suffix, or formatting inconsistencies. These errors can lead to authentication failures, but Mailforge ensures every record is consistent and reliable, improving deliverability across the board.
The platform can complete the entire authentication setup in about five minutes. Once a domain is added, Mailforge generates the required keys, creates the DNS records, and automatically pushes them to your DNS provider. This uniformity ensures that all domains are configured correctly, avoiding issues where some work while others don’t due to setup discrepancies.
Handling Multiple Domains and Mailboxes
Managing large-scale email operations requires tools that go beyond automation. Mailforge addresses this need with features like multiple workspaces, domain transfers, and bulk DNS updates, making it easier to handle even the most complex setups.
The multiple workspaces feature helps you organize domains based on clients, campaigns, or projects. This is especially useful for agencies managing email infrastructure for multiple clients. It allows you to keep each client’s domains separate while maintaining centralized control over their authentication settings. If you need to move domains between projects or teams, you can do so without reconfiguring DKIM settings.
With bulk DNS updates, you can update multiple domains at once - whether it’s rotating keys or modifying authentication settings. This is a lifesaver when managing hundreds of domains that all require the same changes. Instead of tackling updates one by one, you can apply them across your entire operation in just a few clicks.
Mailforge is designed to handle hundreds or even thousands of domains and mailboxes in minutes, without sacrificing performance. Whether you’re running a small agency with 50 domains or managing an enterprise with thousands, the platform remains fast and responsive.
When it comes to cost, Mailforge offers a pricing structure that’s ideal for large-scale operations. At $484 per month for 200 mailboxes, it’s a more affordable option compared to Google Workspace ($1,680 per month) or Microsoft 365 ($1,200 per month) for the same number of accounts. This makes it a cost-effective choice for businesses looking to scale their email operations.
Using Mailforge with Other Email Tools
Mailforge’s automation and scalability integrate smoothly with other tools in your email outreach stack, allowing you to maintain your existing workflows while benefiting from its automated DKIM management.
When paired with Salesforge, you get a streamlined cold outreach system where your domains are authenticated from the start. The DKIM records Mailforge generates work seamlessly with Salesforge’s sending capabilities, ensuring your campaigns launch with optimal deliverability.
Warmforge integration makes the email warming process effortless. Since Mailforge handles DKIM authentication upfront, Warmforge can immediately start building sender reputation without waiting for manual DNS configuration.
Combine this with Leadsforge for lead generation, and you’ve got a complete outreach pipeline. Every component works together, avoiding the all-too-common problem of losing great leads due to deliverability issues caused by poor authentication.
The centralized management dashboard ties it all together. Instead of hopping between platforms to troubleshoot DKIM failures, you can monitor and resolve authentication issues for all your domains in one place. This unified approach saves time and ensures your entire email stack operates smoothly.
For agencies and enterprises running complex outreach campaigns, this level of integration is a game changer. With over 10,000 businesses already using Mailforge, the platform has proven it can scale from small teams to massive organizations while maintaining its efficiency and automation capabilities.
Conclusion
Setting up DKIM for email authentication involves a few key steps: generating cryptographic keys, updating DNS records, configuring your email server, and thoroughly testing the setup. While these tasks are relatively straightforward for a single domain, they can quickly become a logistical challenge when managing multiple domains or scaling up your email operations.
By securing your emails with DKIM, you not only protect them from tampering but also enhance your sender reputation. DKIM plays a critical role in ensuring email deliverability by verifying the legitimacy and integrity of your messages. When combined with SPF and DMARC, it can reduce email spoofing by up to 99% and significantly improve inbox placement rates. Considering that over 80% of phishing attacks exploit domains lacking proper email authentication, implementing DKIM is a non-negotiable step for any serious email strategy.
For businesses managing high-volume email outreach, manually setting up DKIM can introduce delays and errors. This is where Mailforge’s automated DNS configuration becomes a game-changer. By automating the process, Mailforge eliminates common mistakes and speeds up authentication, ensuring smoother operations.
Mailforge also simplifies complex email infrastructures with features like bulk DNS updates and support for multiple workspaces. Whether you’re configuring DKIM for a single domain or thousands of mailboxes, maintaining accuracy and consistency is crucial. Using a 2048-bit key further strengthens authentication and boosts deliverability. For organizations aiming to scale their email systems efficiently, tools like Mailforge transform what was once a time-intensive process into a seamless and dependable solution. With Mailforge, scaling DKIM across domains becomes not only manageable but highly efficient.
FAQs
What should I watch out for when setting up DKIM across multiple domains?
When setting up DKIM for multiple domains, getting the details right is critical. Even small errors, like typos in DNS records or mismatched public and private keys, can cause authentication issues and hurt your email deliverability.
Platforms like Mailforge can make this process much easier. They automate the configuration of DKIM, SPF, and DMARC, ensuring everything is set up correctly while adhering to best practices. This not only saves time but also minimizes the risk of mistakes across your domains.
How does DKIM help improve email deliverability and protect your sender reputation?
DKIM, or DomainKeys Identified Mail, is essential for building trust in your emails. It works by attaching a digital signature to every email you send. This signature acts as proof that the email hasn’t been tampered with during transit and confirms it originates from an authorized domain.
Why does this matter? For starters, it helps your emails avoid the spam folder by boosting their credibility with email providers. Plus, it strengthens your sender reputation - a key factor in ensuring your emails consistently reach your audience. Tools like Mailforge make this process easier by automating DKIM setup alongside other critical protocols like SPF and DMARC, so you can focus on connecting with your audience without worrying about technical hurdles.
Why should you use a 2048-bit key for DKIM, and how does it enhance email security?
Using a 2048-bit key for DKIM (DomainKeys Identified Mail) is highly recommended because it offers stronger encryption, making it much tougher for attackers to exploit. Unlike shorter keys, a 2048-bit key provides a higher level of security, helping to protect against threats like email spoofing and phishing.
When you implement a 2048-bit key, you strengthen the authenticity of your email communications and minimize the chances of unauthorized access or manipulation. This added layer of protection is particularly crucial for businesses that deal with sensitive data or manage extensive email campaigns.