How DMARC Updates Affect Cold Email
DMARC updates are reshaping cold email strategies. If you're sending over 5,000 emails daily to Gmail or Yahoo users, you now need a proper DMARC policy to avoid being blocked. Starting February 2024, major providers like Google and Yahoo require DMARC compliance, and stricter standards rolled out in 2025 mean non-compliance leads to outright email rejection.
Key takeaways:
- DMARC Basics: DMARC works with SPF and DKIM to authenticate emails and prevent spoofing. Policies include
none,quarantine, andreject. - New Rules: Gmail and Yahoo now enforce DMARC for bulk senders. Gmail's Postmaster Tools use a binary compliance system - partial compliance isn’t enough.
- Risks: Without DMARC, emails are flagged as spam or blocked, damaging your domain's reputation. Misaligned SPF, DKIM, or DNS errors can trigger failures.
- Solutions: Start with a
p=nonepolicy to monitor issues. Gradually move to stricter policies (p=quarantineorp=reject). Use top cold email tools like Mailforge for automated DNS setup and Warmforge to maintain sender reputation.
DMARC compliance is no longer optional if you rely on cold email campaigns. Proper setup ensures your emails reach inboxes while protecting your domain from spoofing and deliverability issues.
How DMARC Updates Create Problems for Cold Email
What Changed in DMARC Policies
In 2025, the rules surrounding DMARC enforcement underwent a major overhaul. Google ended its grace period in November 2025, switching from issuing warnings to outright rejecting non-compliant bulk emails at the SMTP level. Microsoft followed suit earlier that year, on May 5, 2025, moving from simply relegating non-compliant emails to the Junk folder to rejecting them entirely.
Here’s an important detail: Google defines a bulk sender as any domain that sends 5,000 or more emails to personal Gmail accounts within a 24-hour period. This threshold applies cumulatively to the primary domain and all its subdomains. Once you hit this limit, your domain is permanently classified as a bulk sender, with no way to reverse the designation.
Adding to the complexity, Google revamped its Postmaster Tools with the launch of version 2. The previous reputation scoring system was replaced with a binary "Compliance Status." Now, partial compliance isn’t good enough - emails that don’t meet the standards are immediately rejected. As James Savard explained on December 5, 2025:
"The change is binary: non-compliant emails now face temporary rate limiting or permanent rejection at the SMTP level. No more spam folder limbo."
Alignment rules have also tightened. Your "From" header must align with either your SPF envelope sender domain or your DKIM signature domain. If there’s any misalignment, authentication fails - even if SPF and DKIM technically pass.
These stricter measures don’t just block emails; they also ripple through your domain’s reputation, creating long-term challenges for email deliverability.
Effects on Domain Reputation and Deliverability
The new DMARC policies trigger a chain reaction that can severely impact your domain’s reputation. Major email providers like Google, Yahoo, Apple, and Microsoft have adopted unified sender standards. This means even one misstep - like a misconfigured DMARC policy - can tank your deliverability across the board.
Without a proper DMARC setup, your emails are far more likely to get flagged as spam or outright rejected. This problem is compounded by the fact that many businesses still lag behind in DMARC adoption. Milena Baghdasaryan, a Content Specialist at PowerDMARC, highlights the risks:
"The wrong cold email DMARC setup can completely ruin your email deliverability and overall marketing campaign."
Moving from a monitoring policy (p=none) to enforcement (p=quarantine or p=reject) is now essential for ensuring your emails land in inboxes. However, implementing these changes too hastily can backfire. Hagop K. from EasyDMARC warns:
"Enforcing DMARC too quickly can actually cause more harm than good, like blocking your own legitimate emails from reaching customers or partners."
When your domain’s reputation takes a hit, it creates a cascade of technical difficulties, making it even harder to maintain a reliable cold email strategy. For more cold email infrastructure tips and deliverability guides, stay updated with the latest industry news. These challenges underline the importance of careful planning and execution when adapting to the new DMARC standards.
(function(d,u,ac){var s=d.createElement('script');s.type='text/javascript';s.src='https://a.omappapi.com/app/js/api.min.js';s.async=true;s.dataset.user=u;s.dataset.campaign=ac;d.getElementsByTagName('head')[0].appendChild(s);})(document,372145,'bgla6zdvtvvykvmfmifs');
Technical Challenges DMARC Updates Create for Cold Email Infrastructure
Problems with Domains That Lack Authentication
The recent policy updates have created a host of technical hurdles for domains without proper authentication. If a domain lacks SPF, DKIM, and DMARC protocols, the consequences are immediate and severe. Bounce rates for unauthenticated domains can soar to 19%, while domains with proper configurations experience much lower rates. And it’s not just about emails landing in spam folders - major email providers now outright reject non-compliant messages at the SMTP level, preventing them from even reaching inboxes.
One major issue is the SPF record limit of 10 DNS lookups. If this limit is exceeded, it triggers a "permerror" status, resulting in an authentication failure. This becomes particularly tricky for businesses using multiple third-party services, as each service adds its own DNS lookups to the SPF chain, quickly eating up the limit.
Another common pitfall is domain alignment failures. For DMARC compliance, your "From" address must match either the SPF Return-Path domain or the DKIM signature domain. Many cold email senders inadvertently violate this rule, especially when third-party tools substitute their own bounce domains. As Matthew Vernhout, Principal Email Advisor at Email Industries, explains:
"A well-configured SPF record keeps spammers out and your reputation intact. But a single typo? It's like handing the keys to your domain to the bad guys."
Reverse DNS (rDNS) mismatches also rank high among the reasons for delivery failures. If a mail server’s IP address doesn’t match its hostname via a proper PTR record, receiving servers often flag the email as suspicious. Syntax errors, such as multiple SPF records or duplicate "v=spf1" tags, can further invalidate authentication efforts.
On top of these domain-specific challenges, shared infrastructure adds another layer of complexity under stricter DMARC enforcement.
Issues with Shared Cold Email Infrastructure
Shared infrastructure brings its own set of risks, particularly under stricter DMARC rules. When multiple senders share the same IP pools or generic Return-Path domains, one sender’s poor practices can harm everyone else’s email deliverability. This "noisy neighbor" problem means your domain’s reputation is tied to the actions of others using the same infrastructure.
The situation becomes even more complicated because shared systems often rely on centralized bounce domains that don’t align with individual sending domains. This misalignment causes automatic DMARC failures, even if your SPF and DKIM records are technically correct. The issue isn’t with the authentication protocols themselves but with how shared systems implement them across multiple users.
DNS configuration in shared environments can also spiral out of control. Each additional sender adds DNS lookups to shared SPF records, and it doesn’t take long to hit the 10-lookup limit. When that limit is exceeded, authentication fails - not just for the sender who caused the issue but for everyone relying on that shared infrastructure.
The new standards leave no room for partial compliance. Your infrastructure either fully passes authentication checks, or it fails entirely. And failure means your emails won’t get delivered, plain and simple.
How to Set Up DMARC for Cold Email Compliance
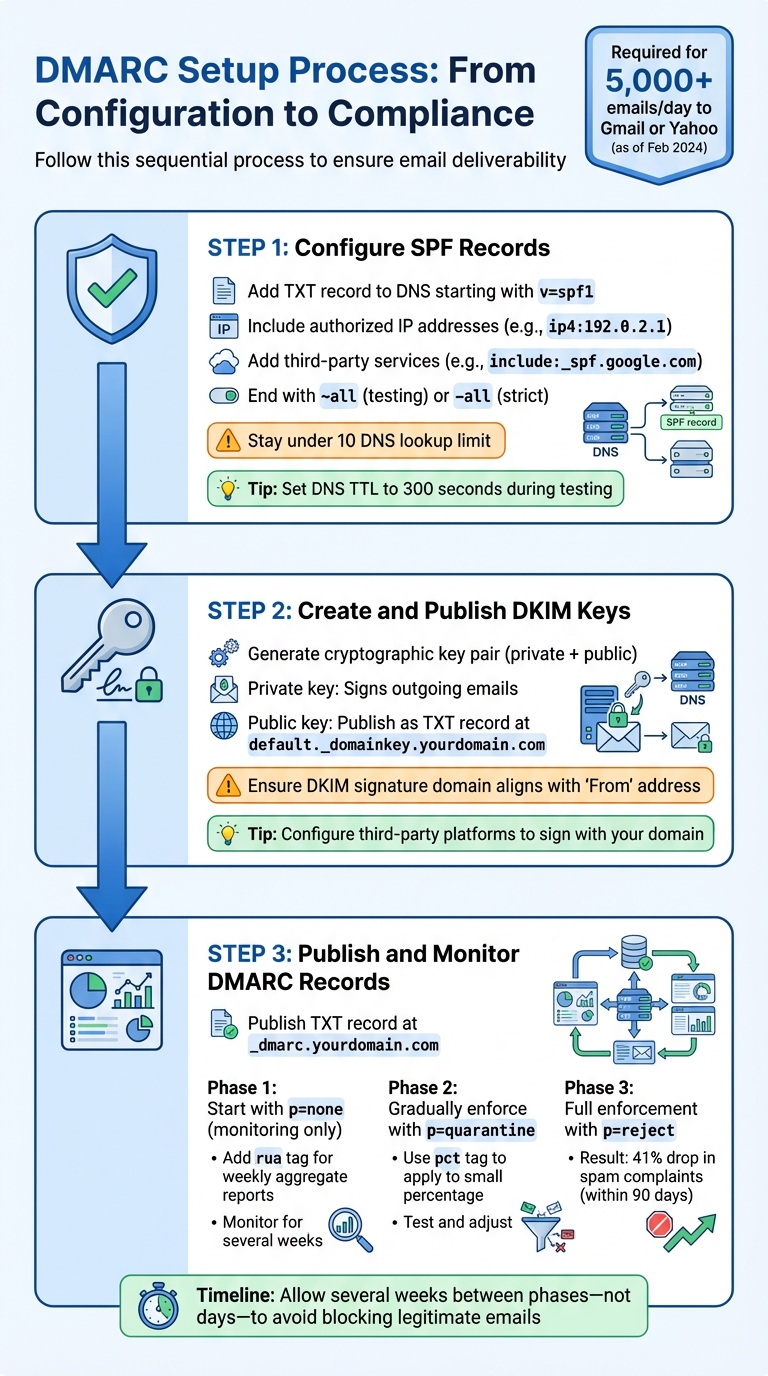
DMARC Implementation Guide: 3-Step Setup Process for Cold Email Compliance
Dealing with the challenges of recent DMARC updates can feel daunting, but setting up DMARC correctly is your best defense against email deliverability issues. For anyone relying on cold email campaigns, DMARC compliance is no longer optional. Starting February 2024, major email providers like Google and Yahoo will require SPF, DKIM, and DMARC for all bulk email senders. The setup process follows a specific order: configure SPF first, then DKIM, and finally DMARC. Each step builds on the previous one, creating a solid foundation for reliable email delivery.
However, jumping straight to a strict p=reject policy without proper testing can cause problems, including blocking legitimate emails. It’s smarter to start with a monitoring policy. This lets you gather data on email authentication issues and gradually tighten enforcement as you resolve any problems.
How to Set Up SPF Records
SPF (Sender Policy Framework) is a protocol that tells email servers which IP addresses are authorized to send emails on behalf of your domain. To set it up, add a TXT record to your domain’s DNS settings. The record should start with v=spf1, followed by the mechanisms that define your authorized senders. For example:
ip4:192.0.2.1authorizes a specific IPv4 address.include:_spf.google.comcovers all Google mail servers.
End the record with ~all during testing or -all for strict enforcement once you’re confident everything works.
One important thing to keep in mind: SPF has a 10 DNS lookup limit. Each include: directive counts as one lookup, and exceeding this limit will result in a "PermError", breaking your email authentication. To make testing smoother, lower your DNS TTL (Time to Live) to 300 seconds for quicker propagation. Once you’ve verified everything, you can increase it back to a higher value.
How to Create and Publish DKIM Keys
DKIM (DomainKeys Identified Mail) adds an extra layer of security by attaching a digital signature to your emails. This signature ensures that emails haven’t been tampered with during transit. Setting up DKIM involves generating a pair of cryptographic keys:
- A private key used to sign outgoing emails.
- A public key that you publish as a TXT record in your DNS settings, typically at a subdomain like
default._domainkey.yourdomain.com.
A common pitfall is misalignment between the DKIM signature domain and the 'From' address. This mismatch can cause DMARC to fail. If you’re using a third-party email platform, make sure it signs emails using your domain instead of its own.
How to Publish and Monitor DMARC Records
Once SPF and DKIM are configured, it’s time to bring them together with DMARC. DMARC works by tying SPF and DKIM to a single policy, instructing email servers on how to handle messages that fail authentication. To get started, publish a TXT record at _dmarc.yourdomain.com with a monitoring policy (p=none). Use the rua tag to receive weekly aggregate reports on how your emails are being handled.
As you gain confidence that your legitimate emails are passing authentication, you can gradually enforce stricter policies. For example, you might start with p=quarantine and apply it to a small percentage of your traffic using the pct tag. Over time, you can scale up to a full p=reject policy. One SaaS company reported a 41% drop in spam complaints within 90 days of implementing a reject policy.
Hagop K. from EasyDMARC offers a word of caution:
"Enforcing DMARC too quickly can actually cause more harm than good, like blocking your own legitimate emails from reaching customers or partners."
It’s wise to give yourself several weeks - rather than just days - to transition from monitoring to enforcement. This allows time to fix any issues that arise.
Using Mailforge for Automated DNS Setup
Manually configuring DNS settings for multiple domains can be a time-consuming and complex task. That’s where Mailforge comes in. This platform automates the setup of SPF, DKIM, and DMARC across all your domains and mailboxes. It ensures proper configuration, domain alignment, and bulk DNS updates without requiring manual effort.
With Mailforge, setup time shrinks from hours or even days to just about 5 minutes. The platform also handles tricky details, like staying within SPF lookup limits and rotating DKIM keys, while maintaining strong DMARC policies. Designed for cold outreach, Mailforge uses shared IP pools to deliver high performance and ensures compliance with the latest email standards. It also offers flexible pricing for businesses of all sizes.
For those needing private infrastructure, Infraforge provides similar automation but with dedicated IPs, multi-IP provisioning, and API access. If you’re using Google Workspace or Microsoft 365 mailboxes with U.S.-based IPs, Primeforge offers automated DNS setup tailored to these platforms.
How to Maintain Deliverability After DMARC Implementation
Setting up DMARC is just the first step. The real challenge lies in maintaining strong email deliverability as your operations grow. Even with authentication in place, you’ll need the right infrastructure and tools to ensure your emails consistently land in inboxes - not spam folders.
Using Mailforge for Scalable Cold Email Infrastructure
Mailforge offers a scalable, DMARC-compliant solution for managing cold email infrastructure. It’s designed to handle hundreds - or even thousands - of mailboxes while automating the ongoing management of email authentication. With features like shared IP pools and domain masking, Mailforge helps protect your sender reputation by hiding your domain structure. This service is available for just $2 per domain per month.
What’s more, Mailforge integrates seamlessly with any email-sending software and includes bulk DNS updates. This allows you to rotate DKIM keys or adjust SPF records across all domains with a single click, saving time and effort.
Danny Goff, Director of Sales at Propeller, highlights its impact:
"We often hear 10x improvement as a target among startups, when it comes to cold email infrastructure setup, Mailforge provides 100x improvement!"
Even with flawless DMARC configuration, it’s essential to limit each inbox to sending 20–30 emails per day to safeguard your sender reputation. Additionally, warming up accounts strategically is key to maintaining deliverability.
Improving Deliverability with Warmforge
Warmforge is another crucial tool for keeping your emails out of spam folders. It focuses on building and sustaining a strong sender reputation by gradually warming up email accounts and testing inbox placement. Warmforge uses a Heat Score™ system to measure each mailbox’s readiness for sending emails and provides a structured warm-up schedule. Early on, targeting your most engaged recipients - those likely to open and click - can accelerate reputation building.
Another critical factor in email delivery is reverse DNS (PTR) records. Missing or incorrect PTR records account for 80% of delivery issues, and Warmforge actively monitors this alongside engagement metrics. Best of all, Warmforge is included at no additional cost with any Salesforge subscription, making it a budget-friendly way to maintain deliverability after implementing DMARC.
Connecting Salesforge for Better Outreach
Salesforge completes the system by managing your outreach campaigns for maximum performance. It works hand-in-hand with Mailforge’s infrastructure and Warmforge’s reputation management to ensure your campaigns run smoothly. Salesforge supports multi-channel sequences, combining email and LinkedIn, and allows unlimited senders to prevent overloading any single mailbox. Real-time Health Scores alert you if a mailbox’s reputation dips below 97%, signaling when it’s time to pause campaigns and refresh your setup.
When integrating Salesforge with Mailforge, it’s best to start with a DMARC policy of p=none. This allows you to collect reports and confirm that all sending sources are properly authenticated. Once everything checks out, you can shift to stricter policies. For aggressive outreach, consider using subdomain isolation (e.g., outreach.yourcompany.com) to safeguard your main domain.
Together, Mailforge, Warmforge, and Salesforge create a comprehensive system for maintaining deliverability after DMARC implementation. For example, setting up Mailforge with 200 mailboxes costs about $484 per month. This integrated approach is not only effective but also affordable, making it a practical choice for businesses of all sizes while ensuring DMARC compliance.
Conclusion
If you’re sending over 5,000 emails a day to major providers like Google, Yahoo, or Microsoft, DMARC compliance isn’t optional - it’s a must. And the benefits are clear: SaaS companies that adopted DMARC saw a 94% decrease in phishing attempts. This shows how proper email authentication safeguards not just your domain but also your recipients.
By moving from monitoring (p=none) to enforcement (p=quarantine or p=reject), you’re not only blocking unauthorized emails but also strengthening your sender reputation. This shift builds trust with inbox providers, ensuring your emails land where they’re supposed to.
Mailforge makes this process effortless. It automates DNS setup, handles authentication records with one-click bulk updates, and provides DMARC-compliant infrastructure - all for just $2 to $3 per mailbox per month. For example, configuring 200 mailboxes would cost approximately $484 per month, and the setup for all domains can be completed in under 10 minutes.
When paired with tools like Warmforge for reputation management and Salesforge for executing campaigns, you get a complete system designed to maintain deliverability while scaling your outreach. The foundation of this system? Proper email authentication, consistent monitoring of DMARC reports, and infrastructure tailored specifically for cold email - not generic business tools.
DMARC updates don’t have to disrupt your campaigns. With the right tools and setup, you can keep your deliverability strong while meeting compliance standards that benefit everyone in the email ecosystem.
FAQs
What is DMARC, and why does it matter for cold email campaigns?
DMARC, short for Domain-based Message Authentication, Reporting & Conformance, is an email authentication protocol designed to work hand-in-hand with SPF and DKIM. Its primary job? To confirm that the emails sent from your domain are legitimate. For cold email campaigns, this is a game-changer. It boosts the chances of your messages landing in recipients' inboxes by improving deliverability and reducing the likelihood of them being marked as spam.
But that’s not all. DMARC also acts as a shield for your domain, protecting it from spoofing and phishing attacks - threats that can tarnish your brand's reputation. Plus, major email providers like Google and Microsoft expect proper authentication. Without it, your outreach efforts might not even make it past their filters.
How do I keep my domain compliant with updated DMARC rules for cold email campaigns?
To keep your domain aligned with the latest DMARC updates and ensure strong email deliverability, here’s what you need to do:
- Set up SPF and DKIM properly: Double-check that every IP and service sending emails on your behalf is authorized in your SPF record. Also, make sure your DKIM keys are configured to sign messages correctly. Both need to align with your domain for maximum security.
-
Start with a monitoring DMARC policy: Begin with
p=noneto collect reports without affecting email delivery. Regularly review these reports to spot any misalignments or unauthorized senders, and address issues as they arise. -
Tighten your DMARC policy gradually: After ensuring your domain consistently passes SPF and DKIM checks, shift from
p=nonetop=quarantine, and eventually top=reject. This progression helps you block unauthorized emails while minimizing disruptions. - Automate DNS updates: Tools like Mailforge can simplify the process of managing SPF, DKIM, and DMARC records across multiple domains. Automation reduces the risk of errors and keeps your records current.
By carefully monitoring reports, adjusting your policy step by step, and using automation tools, you can maintain compliance with DMARC standards and safeguard your email deliverability.
What happens if I don’t use DMARC for my cold email campaigns?
Not setting up DMARC can seriously impact both the effectiveness and security of your cold email campaigns. Without it, your emails are far more likely to end up in spam folders - statistics show that up to 46% of messages might fail to make it to recipients' inboxes. Even worse, your domain becomes vulnerable to spoofing and phishing attacks, which can tarnish your reputation and erode trust.
On top of that, major email providers like Google and Yahoo expect DMARC compliance to ensure smooth deliverability. Skipping this step could mean failing to meet their standards, making it even harder to get your emails seen. Taking the time to implement DMARC is a smart move to safeguard your domain and improve the chances of your emails landing where they’re supposed to.