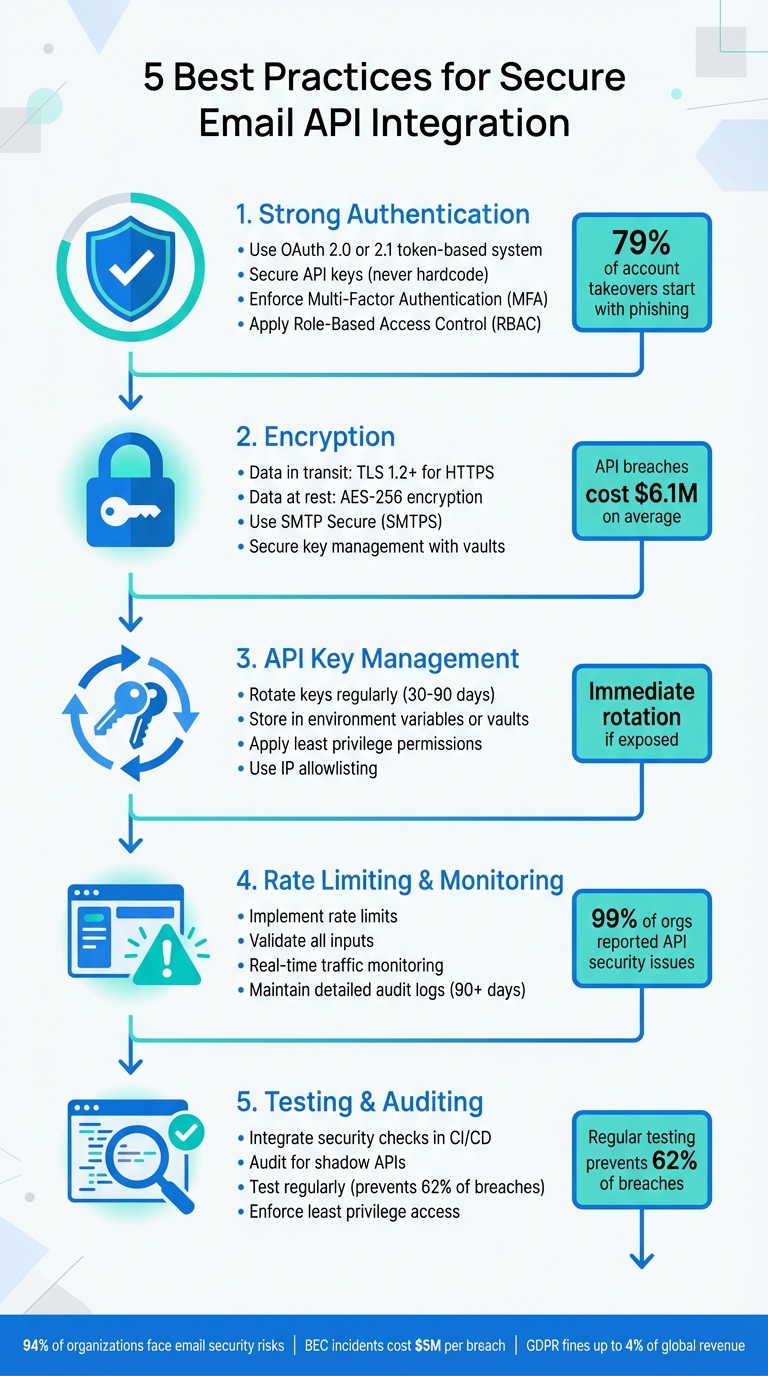
5 Best Practices for Secure Email API Integration
Securing your email API integration is critical to protect sensitive data, maintain compliance, and avoid costly breaches. Here are the five key practices every organization should follow:
- Strong Authentication: Use OAuth 2.0 or 2.1, secure API keys, enforce Multi-Factor Authentication (MFA), and apply Role-Based Access Control (RBAC) for limited permissions.
- Encryption: Ensure data is encrypted in transit (TLS 1.2 or higher) and at rest (AES-256). Use SMTP Secure (SMTPS) for email traffic and manage encryption keys securely.
- API Key Management: Rotate keys regularly, avoid hardcoding them, use environment variables or vaults, and restrict permissions to the minimum required.
- Rate Limiting and Monitoring: Implement rate limits, validate inputs, monitor traffic in real time, and maintain detailed audit logs to detect anomalies and ensure compliance.
- Testing and Auditing: Continuously test APIs, audit for vulnerabilities, and apply least privilege access to mitigate risks.
These steps help prevent data breaches, safeguard your sender reputation, and ensure compliance with regulations like GDPR and HIPAA. For a streamlined solution, platforms like Mailforge simplify security configurations and monitoring for $33 per month (billed annually).
5 Best Practices for Secure Email API Integration
1. Use Strong Authentication and Authorization
Authentication and Authorization Methods
When it comes to securing email API integrations, OAuth 2.0 is widely regarded as the go-to solution. It eliminates the need to share raw credentials by using a token-based system. Think of it like handing someone a valet key instead of giving them full access to your car. The newer OAuth 2.1 builds on this by making PKCE (Proof Key for Code Exchange) mandatory and removing less secure implicit flows, further enhancing security. Beyond OAuth, it’s critical to ensure that sensitive API keys are never exposed.
API keys, while a basic form of authentication, can become a serious security risk if mishandled. A cautionary tale: in July 2025, xAI accidentally published a private API key on GitHub. This misstep allowed unauthorized access to over 50 language models until GitGuardian flagged the issue. To prevent such breaches, API keys should never be hardcoded into client-side code or shared in public repositories. Instead, store them securely in environment variables or use dedicated vault solutions.
For added security, robust access controls are a must. Role-Based Access Control (RBAC) is an effective way to manage permissions by assigning them based on specific roles. For instance, an Admin might have full access to API configurations and billing, while a Support team member could be restricted to view-only access for activity logs. This aligns with the Principle of Least Privilege, ensuring users only have access to the functions they absolutely need. For even finer control, Attribute-Based Access Control (ABAC) can incorporate variables like IP address, time of access, or device type.
Another essential layer of security is Multi-Factor Authentication (MFA), which should be mandatory for all API access. Given that 79% of account takeover attacks begin with phishing emails that steal passwords, MFA adds an extra barrier. Even if credentials are compromised, attackers can’t proceed without the second verification factor. For example, in January 2023, T-Mobile suffered an API breach affecting 37 million users - their eighth data breach since 2018. This incident underscores the importance of strong authentication measures. By layering these methods - tokens, keys, access controls, and MFA - you create a robust defense for your email API integrations.
2. Encrypt Data in Transit and at Rest
Encryption Protocols and Practices
After implementing strong authentication measures, the next step in securing your API communication is encrypting data both in transit and at rest. Encryption acts as the final safeguard - if attackers manage to infiltrate your network, encrypted data remains indecipherable.
For data in transit, always use HTTPS with TLS 1.2 or higher for API communications. TLS encrypts the data traveling between systems, making it unreadable to anyone attempting to intercept it. This is one of the most effective ways to prevent man-in-the-middle attacks. When it comes to data at rest, such as subscriber details, campaign templates, or analytics data, rely on AES-256 encryption. This ensures that even if someone gains unauthorized access to your storage, the data remains protected.
"Encryption ensures that the content remains unreadable even if intercepted, making it useless for the criminal." - Nylas
For securing email traffic, enforce SMTP Secure (SMTPS) with TLS. This is far superior to relying on opportunistic TLS, which can fall back to unencrypted delivery if the recipient's server doesn't support encryption. By enforcing TLS, you guarantee that emails are never transmitted over unprotected connections. Additionally, for highly sensitive information like authentication tokens or personally identifiable information (PII), consider application-level encryption using AES-256. This adds another layer of security, ensuring that even if TLS fails, the data remains protected.
The financial consequences of weak encryption can be staggering. API breaches cost organizations an average of $6.1 million, while inadequate API security measures contribute to global losses of $87 billion. Regulations like GDPR impose fines of up to 4% of global revenue for data breaches. Specific industries face even stricter requirements: for example, healthcare providers must comply with HIPAA's mandate for end-to-end encryption and a 7-year data retention policy, while companies handling credit card data must meet PCI DSS standards, including encryption and 1-year audit trails.
Effective encryption isn't just about using the right algorithms. Key management plays a critical role in securing your data. This includes securely generating, storing, distributing, rotating, and retiring cryptographic keys. Instead of embedding keys directly in your application, use dedicated secret management tools like AWS KMS, Hashicorp Vault, or Google Cloud Secret Manager. To avoid introducing vulnerabilities, rely on trusted cryptographic libraries like libsodium rather than attempting to build custom solutions.
3. Manage and Rotate API Keys Regularly
API Key Management and Rotation
In addition to strong authentication and data encryption, managing API keys effectively is a critical step in safeguarding your email infrastructure. Think of API keys as the keys to your kingdom - if they fall into the wrong hands, attackers can exploit them to send unauthorized emails, access sensitive information, or disrupt your operations. Regularly rotating keys and adhering to the principle of least privilege can significantly enhance your security.
Never hardcode API keys into your source code or mobile scripts. If these keys are exposed - whether through public repositories or unencrypted channels - they can grant attackers full access to your system. A stark example of this occurred in December 2024 when hackers used a compromised API key from BeyondTrust to break into US Treasury workstations, underscoring the need for consistent key rotation and protection.
The frequency of key rotation depends on your organization's security needs. High-security environments often rotate keys every 30 days, while others dealing with less sensitive data might extend the interval to 6 or even 12 months. However, if a key is exposed or becomes overused, immediate rotation is non-negotiable.
To minimize risk, apply the principle of least privilege using Role-Based Access Control (RBAC). For example, an API key dedicated to sending emails should not have access to analytics or subscriber data. Combine this with IP allowlisting to restrict API calls to trusted IP ranges, which helps mitigate risks even if a key is leaked.
For growing organizations managing more complex email infrastructures, platforms like Infraforge offer tools to create granular, project-specific API keys. These keys come with built-in safeguards like enforced TLS 1.2+ and automated key management systems.
"OAuth 2.0 tosses the old credential-sharing approach in the trash where it belongs, enabling secure, limited access through a clever token system."
– Josh Twist, Co-founder & CEO
For even greater security, consider shifting from static API keys to OAuth 2.0 token-based authentication. This system uses short-lived access tokens and refresh tokens, automating the rotation process and reducing manual effort. Always store your keys securely, using environment variables or vault services like AWS KMS or HashiCorp Vault, rather than embedding them in your codebase. Additionally, implement real-time monitoring to track unusual activity, such as unexpected geographic access or spikes in request volumes, especially following a key rotation.
4. Set Up Rate Limiting, Input Validation, and Monitoring
Monitoring and Input Validation
Rate limiting is a key defense mechanism that limits the number of requests a user can make within a set timeframe. This helps protect your Node.js application from DoS attacks and brute-force attempts. Tools like the express-rate-limit library make it simple to implement rate limiting in your app.
Input validation, on the other hand, ensures all incoming data adheres to strict formatting and security standards. This involves verifying the correct structure of inputs, confirming domain authenticity, and using parameterized queries to secure database interactions. For added security, design your API endpoints to filter data on the server side rather than relying on client-side filtering. This approach minimizes the risk of attackers manipulating requests to access sensitive data. Together, input validation and rate limiting form a strong barrier against potential abuse.
Real-time monitoring is another essential layer of protection. It allows you to track authentication attempts, analyze traffic patterns, and identify geographic anomalies. Given that 99% of organizations reported API security issues in the past year and malicious email activity skyrocketed by 4,151% following ChatGPT's release in late 2022, relying solely on periodic reviews simply won't cut it.
"Your API security strategy needs real-time monitoring, or it simply isn't a strategy at all. Without real-time API security monitoring, you're essentially leaving your door unlocked and hoping nobody tries the handle."
– Martyn Davies, Developer Advocate
In addition to these measures, comprehensive audit logs are indispensable. They not only help with compliance but also serve as a critical tool for forensic analysis. Ensure your logs capture essential details like User IDs, timestamps (formatted as MM/DD/YYYY HH:MM:SS), API endpoints, IP addresses, and HTTP status codes. Research shows that effective logging can lower breach risks by 70% and boost compliance rates by 90%. Retain these logs for at least 90 days to meet compliance standards.
Finally, integrate API security checks directly into your CI/CD pipeline. This ensures that monitoring and security practices are baked into your development process from the ground up, rather than being treated as afterthoughts.
5. Test, Audit, and Apply Least Privilege Access
Testing and Auditing Frequency
Security testing isn’t something you can check off once and forget about. It needs to be part of your ongoing process. For example, you can integrate automated security checks directly into your CI/CD pipeline using tools like Selenium or Cypress. These frameworks can verify email content, links, and deliverability during every deployment. To add another layer of security, rotate API keys every 30 days and update DKIM keys every 6 to 12 months. These steps can help prevent replay attacks, which are a common vulnerability. In fact, regular security testing can prevent up to 62% of breaches and save organizations millions of dollars in potential costs.
Another crucial step is automating the discovery of "shadow" APIs - those that are created without formal security oversight. Including these in your audit cycles ensures no endpoint is left unchecked. Organizations with well-maintained logs have a 50% higher chance of passing compliance audits. Plus, automated log monitoring can cut incident response times by as much as 90%. Using a Security Information and Event Management (SIEM) system to centralize monitoring across multiple APIs can also reduce the time spent preparing for audits by 40%.
Authentication and Authorization Methods
Once you’ve nailed down your testing and auditing processes, it’s time to focus on access control. Enforcing least privilege access is one of the most effective ways to limit the impact of potential breaches. Avoid relying on a single master API key. Instead, assign distinct keys with specific, granular permissions for each task. Implement Role-Based Access Control (RBAC) to ensure non-administrative keys can’t perform high-level functions. For even more control, consider Attribute-Based Access Control (ABAC), which allows you to set restrictions based on criteria like IP address, time of day, or device type.
This approach is especially critical when you consider that 94% of organizations report facing significant email security risks. Properly applying least privilege access could have contained many of these incidents, minimizing their impact.
When it comes to audit logs, make sure they capture all the important details: user IDs, timestamps (formatted as MM/DD/YYYY HH:MM:SS), API endpoints, IP addresses, and HTTP status codes. Protect these logs with AES-256 encryption and enforce strict access controls to prevent tampering. Retain logs for at least 90 days as a standard practice, though certain regulations - like HIPAA and SOX - might require you to keep them for up to 7 years. During testing, use disposable email APIs to safeguard real user data.
Conclusion
These five practices - strong authentication, encryption, regular key rotation, monitoring, and least privilege access - create a solid foundation for securing your email API integration. With 94% of organizations facing serious email security threats, implementing these measures not only protects your data but also safeguards your sender reputation and ensures compliance with regulations like GDPR and HIPAA.
The stakes are high. Business Email Compromise (BEC) incidents cost an average of $5 million per breach. On top of that, GDPR violations can lead to fines of up to 4% of global revenue. And let’s not forget the impact on customer trust - 80% of consumers in developed countries say they’d stop doing business with a company that compromised their data. Clearly, email security isn’t just about IT; it’s about protecting your revenue and reputation.
For those seeking a more streamlined approach, Mailforge offers a solution that takes much of the complexity out of secure email infrastructure. It sets up DKIM, SPF, and DMARC in less than 5 minutes, includes built-in SSL encryption, domain masking, and dedicated IPs - all designed to boost deliverability and maintain compliance. At $33 per month for 10 mailbox slots (billed annually), it’s an affordable option that grows with your business. By combining security with simplicity, Mailforge helps you build a resilient email strategy.
FAQs
What are the advantages of using OAuth 2.0 for secure email API integration?
OAuth 2.0 uses a token-based security system, which means there's no need to share sensitive passwords during interactions. It enables user-approved, limited access to APIs, ensuring interactions remain secure and well-regulated. By keeping authorization separate from authentication, OAuth 2.0 offers more flexibility and makes managing API permissions much simpler.
Another advantage is its ability to streamline credential management. With easy token revocation, OAuth 2.0 minimizes the risk of unauthorized access if credentials are ever compromised. These features make it a dependable option for creating secure and scalable email API integrations.
What is rate limiting, and how does it protect my email API from attacks?
Rate limiting is a protective strategy designed to manage the number of requests an email API can process within a set period. By setting limits on request volumes, it helps defend against threats like DDoS attacks, where attackers flood your system with excessive traffic, and misuse by unauthorized users attempting to exploit your API.
This approach does more than just shield your infrastructure from being overwhelmed. It also ensures that resources are distributed fairly among users. Adding rate limiting to your API integration boosts security and reliability, helping your email systems operate efficiently and without interruptions.
Why is it important to regularly update and rotate API keys?
Keeping your API keys updated and rotating them frequently is an essential step in maintaining security. This practice reduces the window of opportunity for anyone to misuse a compromised key. By doing so, you safeguard sensitive information, lower the chances of expensive security breaches, and ensure your email API integration stays secure and dependable.